Information Security Management (ISMS) Solution
Improve information security and cyber resilience with an ISMS
The GRC Toolbox enables you to build a systematic ISMS, increase the maturity of information security activities and facilitate compliance with security standards from ISO, NIST, BSI, etc. Additionally, our software is designed to align with the Digital Operational Resilience Act (DORA) requirements, ensuring that your digital operations remain resilient against disruptions and comply with EU regulations.






Leading companies use our ISMS solution














GRC Toolbox Insights
Features
Get first insights into the features of our ISMS solution here.
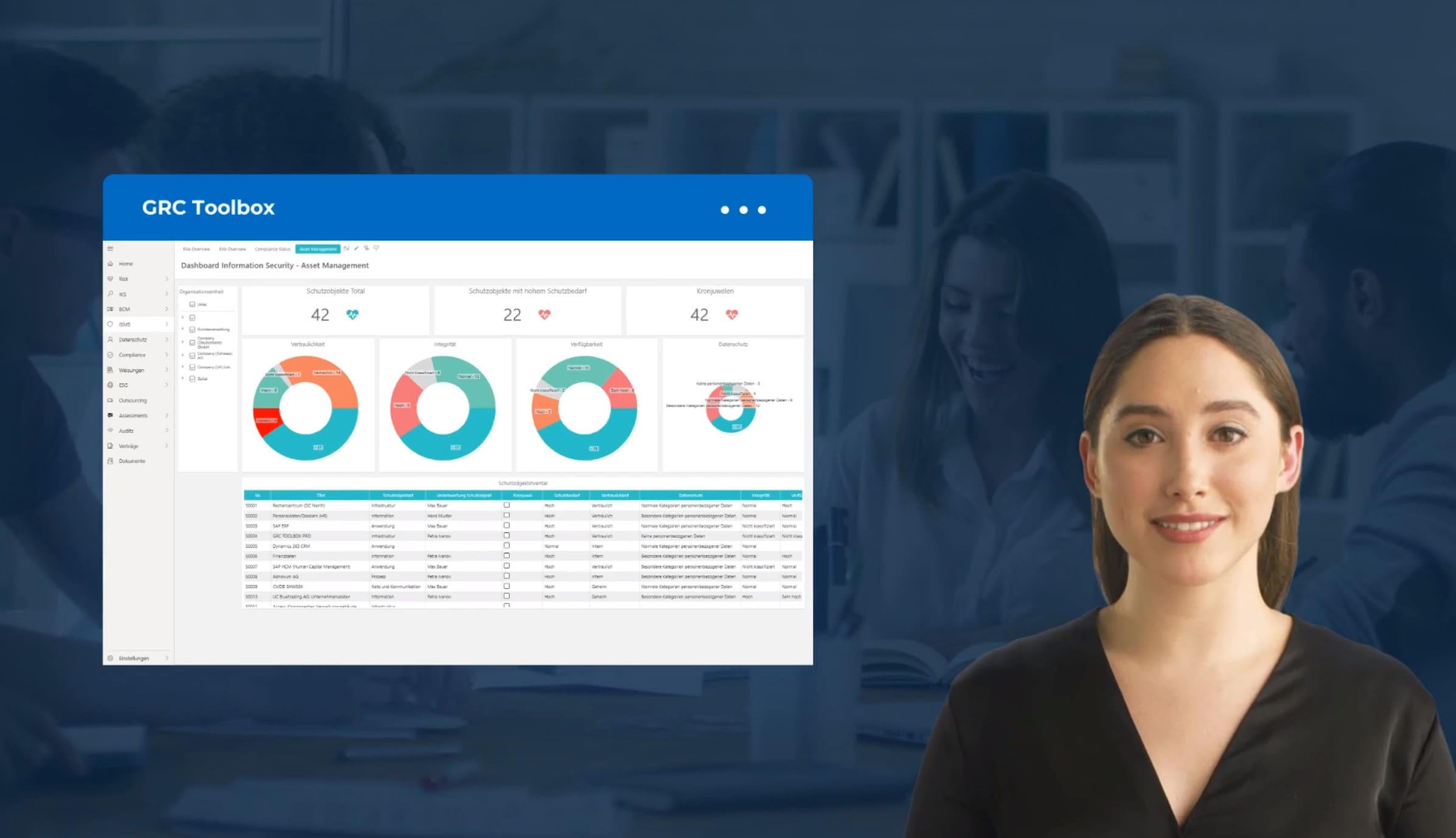
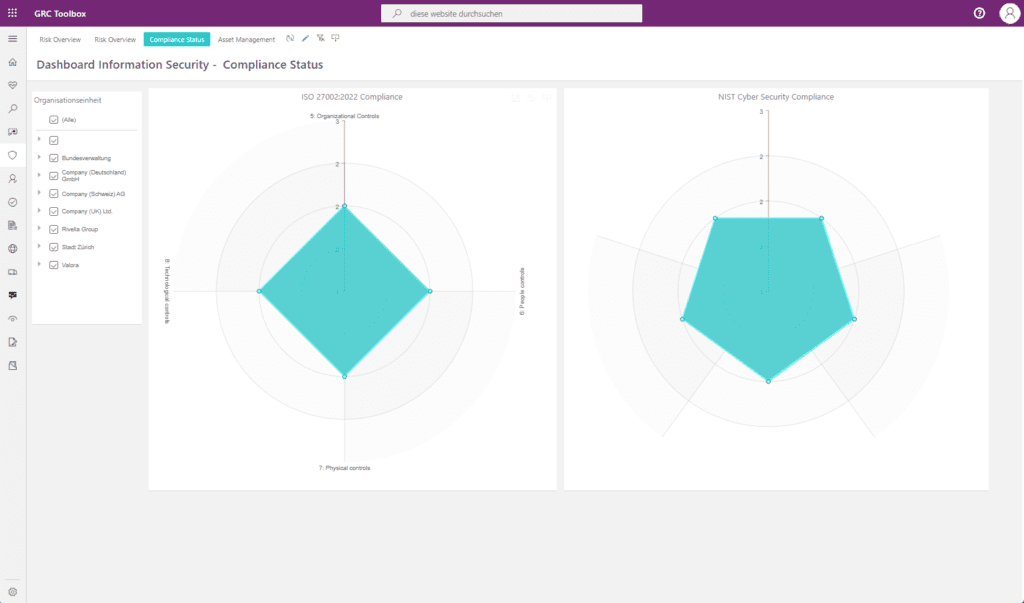
Information Security Reporting
Get information on the numbers and types of assets, the status of security controls, the results of security audits, and the risk status of information security. By monitoring these metrics, potential vulnerabilities and risks are identified and actions can be taken.
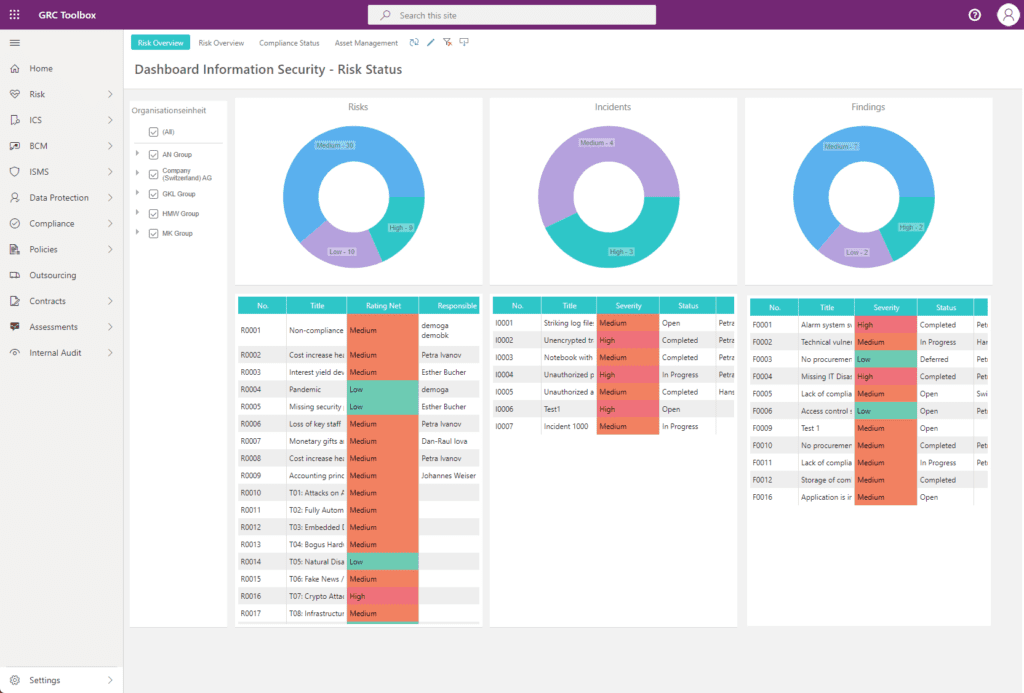
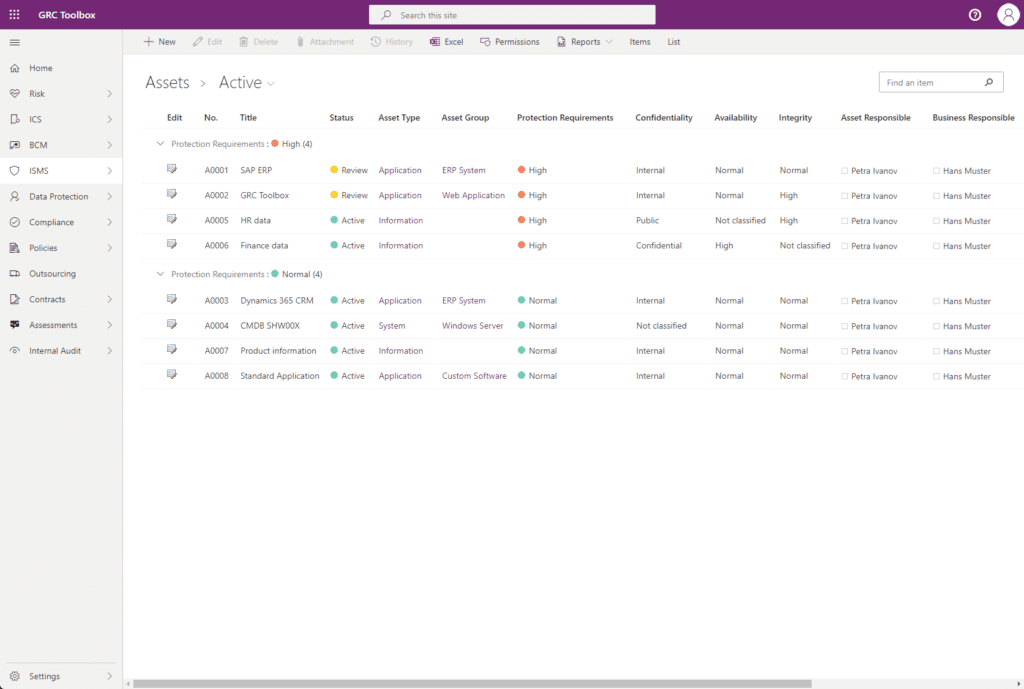
Asset Management and CIA Analysis
This function of the GRC Toolbox covers the identification and recording of an organisation’s critical assets (processes, information, secondary assets). The objective of the protection needs analysis is to determine the need for protection based on the identified assets and, consequently, to define appropriate security measures. The GRC Toolbox is often used to accompany the security process in the context of projects with questionnaires, checklists and workflows and thus to comply with the security and privacy by design principle.
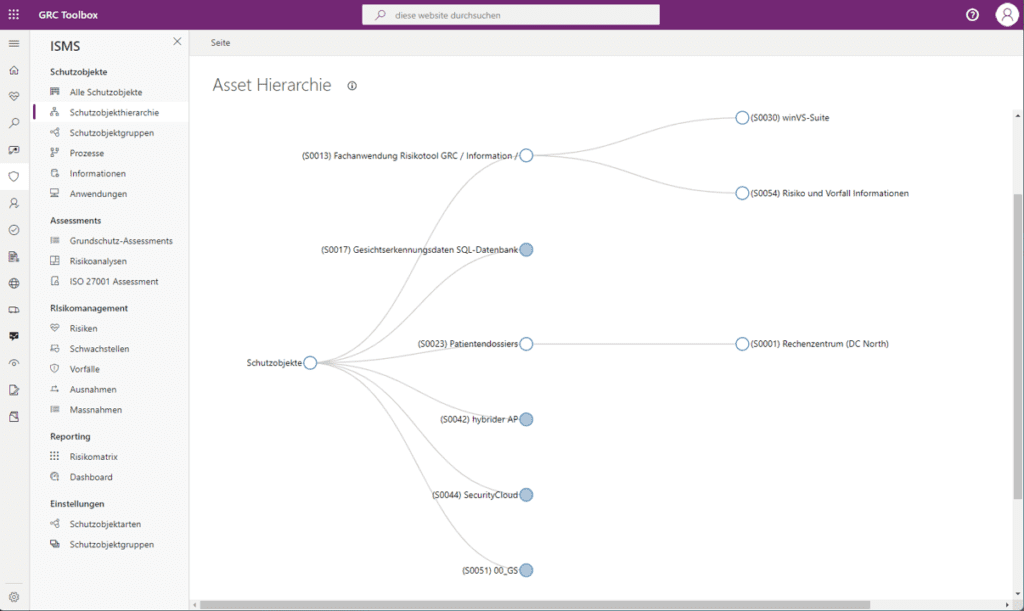
Asset Hierarchy
With our new feature, you can now easily keep track of your asset landscape. Track the complex connections between your assets, including processes, data, systems, applications, and other resources, and see how changes to one asset can impact others. Identify vulnerabilities, risks, and potential bottlenecks to proactively close security gaps and optimize your business operations.
Control and Threat Assessments
The GRC Toolbox Control Assessment is a tool that can provide a quick overview of the existing security level. With the help of a questionnaire, the status of an asset is determined and presented in relation to the degree of fulfillment of the defined security requirements. As a result, the degree of coverage becomes visible and potential areas for improvement or necessary exceptions to security requirements are identified. If required, questionnaires can also be used to carry out detailed risk analyses and, if necessary, to initiate extended security measures.
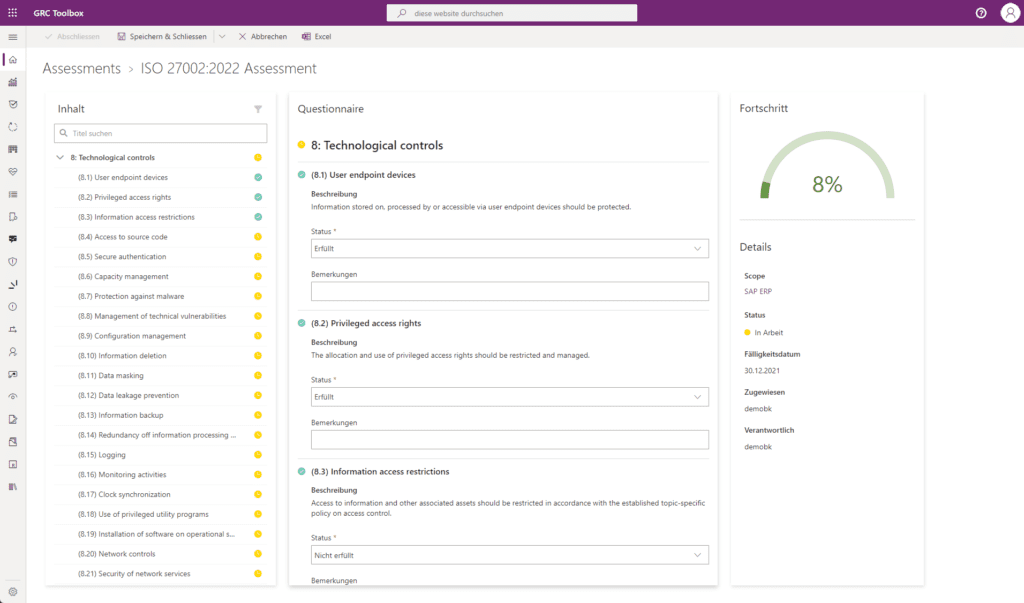
Security Risk Management
The GRC Toolbox has a comprehensive risk management function in accordance with ISO/IEC 27001 and ISO/IEC 27005. Risks can be recorded, analysed, evaluated, prioritised and their treatment planned and executed with the help of workflow support. With dashboards and risk matrices, the risk situation of information security can be made visible at any time.

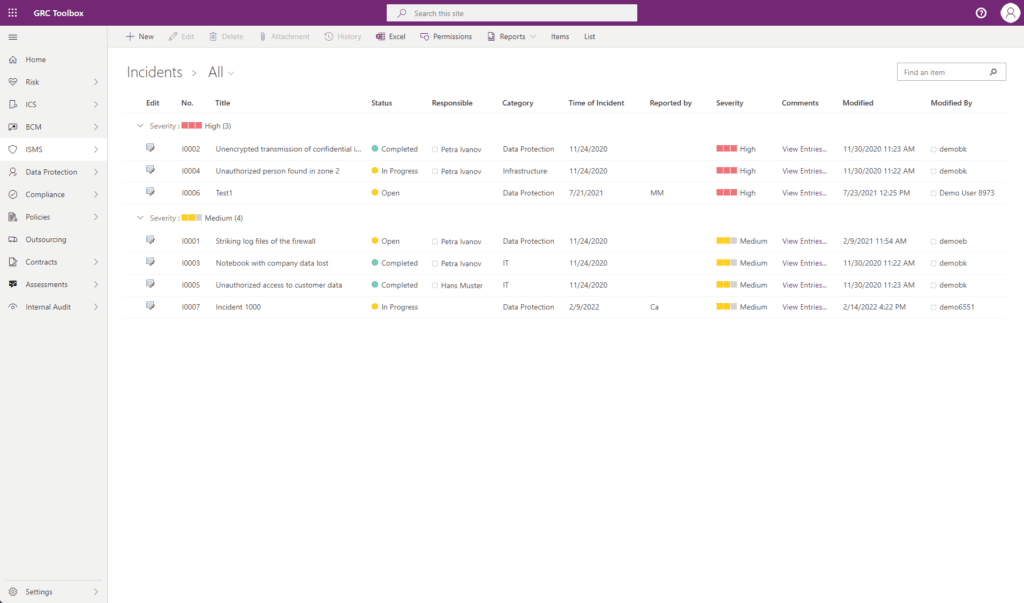
Security incident Management
With the GRC Toolbox, security events and incidents can be recorded and assessed and their handling tracked. In terms of comprehensive incident documentation, causes, effects, and affected assets can be described and the link to risk management can also be made to show the cause-event-impact chain.
Exception Management
Exception management is the process of handling and approving exceptions to an organisation’s established security policies and controls. The GRC Toolbox actively supports identifying exceptions, assessing their impact on the organisation’s security, approving them and monitoring their deadlines. Exception management is an important part of the ISMS as it ensures that exceptions are only approved in exceptional cases and that the impact on the organisation’s security is controlled.

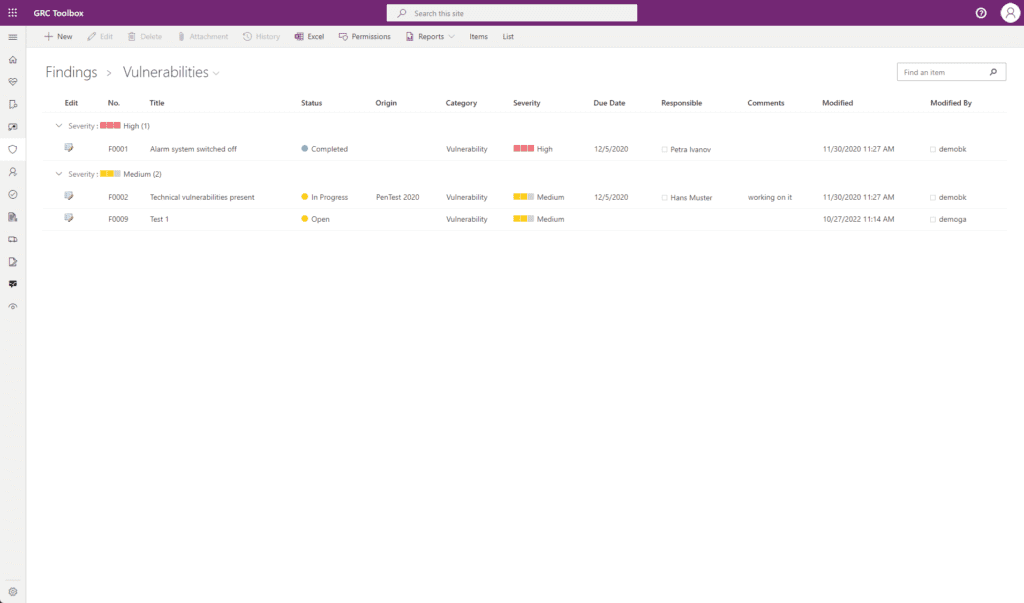
Vulnerability Management
The GRC Toolbox offers the possibility to centrally record, describe and assess identified vulnerabilities and to link them to affected assets and risks. The identified vulnerabilities can also be processed by means of workflow support to ensure a consistent process for the treatment of vulnerabilities.
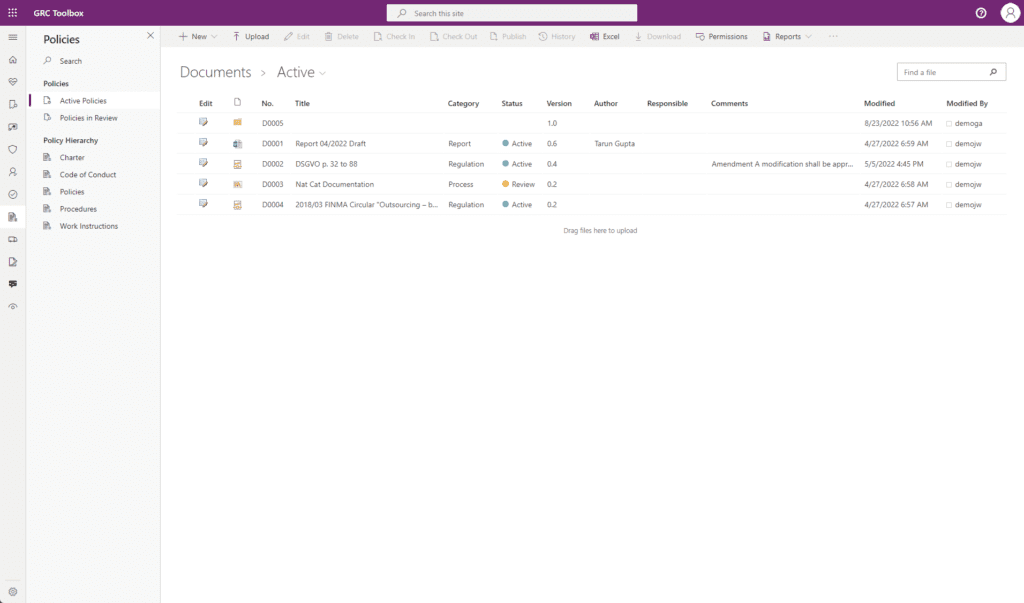
Policy Management
Policy management is the process of developing and implementing policies for information security (and other areas). In this context, the GRC Toolbox with its comprehensive DMS helps to draft the policy documents, review them, have them approved and check them for up-to-dateness and appropriateness in case of changes or in regular operation and to make adjustments if necessary. For ISO/IEC 27001 certification, the policy documents can be referenced in the Statement of Applicability (SoA).
Standards and Frameworks
There are a number of important standards and frameworks in the GRC Toolbox. Some of these are: ISO/IEC 27001, NIST Cyber Security Framework, BSI Standards, IT-Security Baseline, CIS Controls, PCI-DSS, SCF, etc.
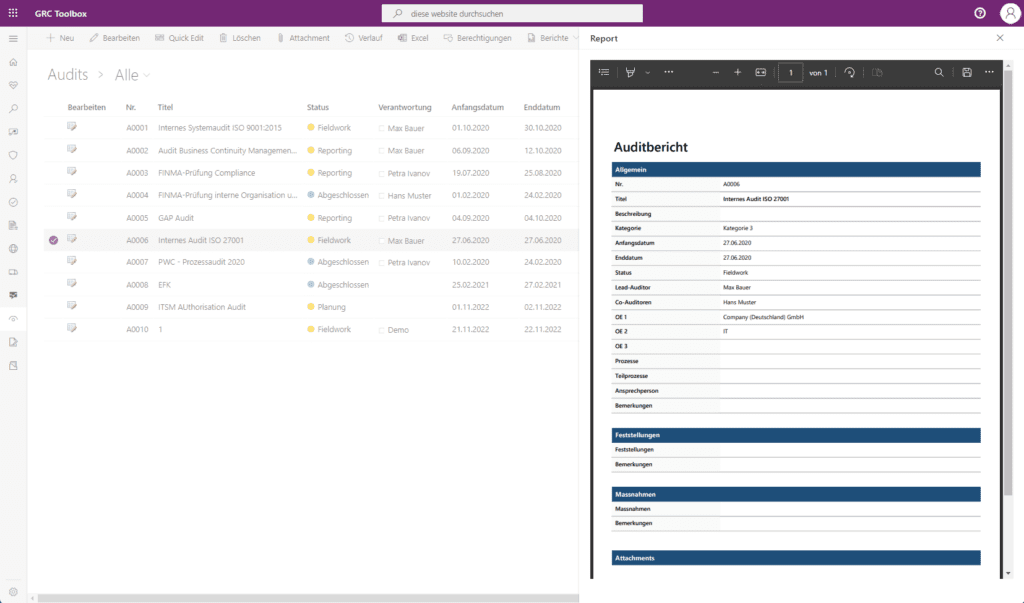
Internal Audit Management
Internal audit management refers to the planning, execution and monitoring of internal information security audits. With the GRC Toolbox, the audits can be recorded centrally, carried out by means of assessments and their results (findings and improvement measures) are documented and implemented.
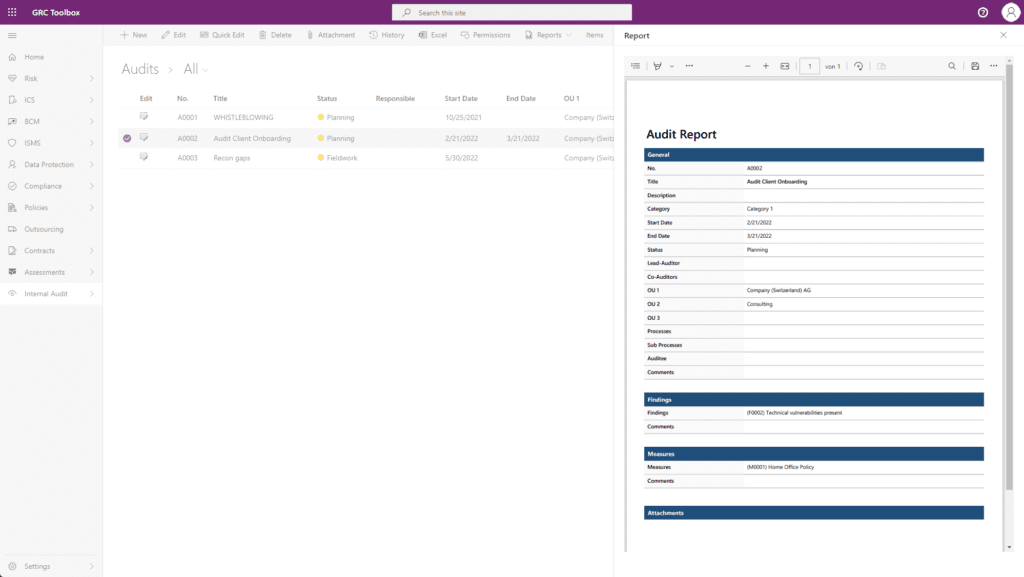
ISO 27001 Certification Support
For ISO 27001 certification projects as well as for the maintenance of certifications, the GRC Toolbox supports the entire spectrum regarding the establishment and operation of an information security management system (ISMS). It helps to fulfill both the normative requirements for the management system from ISO/IEC 27001 as well as the controls from ISO/IEC 27001 Appendix A.












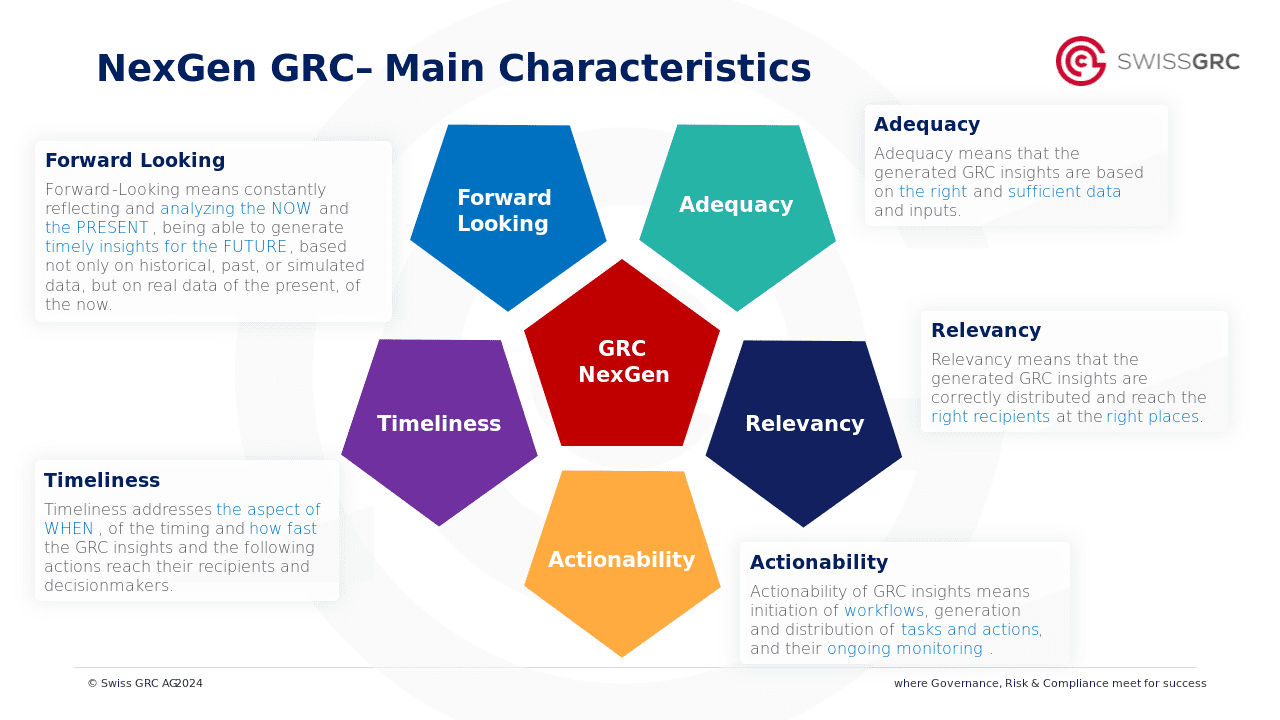
Advantages and added value for your organisation
ISMS with the GRC Toolbox
Centralised and systematic information security management activities
Manage security measures and processes centrally, improving the efficiency and effectiveness of security risk management.
Information security compliance
Monitor and document compliance requirements, such as ISO 27001 and other standards and regulations.
Transparent information security processes
Better understanding of how security risks are identified and assessed, and what actions are taken to minimise those risks.
Cyber Risk Management
Protect IT systems and data more effectively and be better prepared for security incidents in order to have adequate protective measures in place against cyber attacks.
Asset overview with the possibility of interfaces
Create and maintain a complete inventory of all assets and manage the dependencies and links between different assets. External tools such as ServiceNow, LeanIX, etc. can be easily integrated to get base data.
Information security reporting
Generate reports with key information about the organisation’s security maturity using the ISMS Dashboard.
Insurers like Baloise face complex regulatory challenges that require comprehensive GRC software. Choosing Swiss GRC for information security and implementing the GRC Toolbox were the right steps for us. We were impressed by the straightforward integration, the modularity of the GRC Toolbox and the transparent pricing. Our satisfaction so far encourages us to introduce further modules such as data protection to fully meet our requirements. Swiss GRC is our trusted partner to achieve our GRC goals.
Dominik Mutter
Senior Information Security Officer, Baloise
Discover all our solutions around GRC
Create the foundation for a successful GRC strategy. With the GRC Toolbox, you can gradually extend your digital governance, risk and compliance processes to all other GRC areas.
Third-Party Risk Management (TPRM)
Contract Management
Risk Management
Internal Control (ICS)
GRC TOOLBOX
Learn more about our ISMS software
Convince yourself and test all functions of the GRC Toolbox, the user-friendly software for your GRC management.


Mirko Hegi, GRC Expert, PostFinance AG
Right from the start, the cooperation was at eye level and we understood each other, not only on a professional but also on a human level.
Fill out and submit the form, and we will contact you shortly.





 DE
DE



